In a Nutshell
The implementation of Cyber Threat Intelligence (CTI) allows organizations to proactively build cyber resilience and stay ahead of cybercriminals by actively analyzing the tactics, techniques, and procedures (TTPs) of attackers. The foundation of this solution is a comprehensive intelligence cycle—encompassing planning, collection, analysis, and distribution—which supports strategic defensive decision-making. Depending on the organization's needs, CTI operates at the operational, tactical, or strategic levels, enabling not only the development of effective protection mechanisms but also compliance with stringent regulatory requirements set by NIS2 and the DORA regulation. Through a continuous information management process, companies gain the necessary insights to monitor and mitigate threats in real time.
The growing number and complexity of cyber threats, rapid emergence of threat actors, and the introduction of regulations such as DORA and NIS2 require organizations to implement strict security measures as well as continue their efforts to find effective ways to anticipate potential attacks and better protect their assets. In recent years, Cyber Threat Intelligence (CTI) has become an integral part of many cybersecurity strategies. This guide will walk you through key definitions and concepts related to CTI, the essential levels and lifecycle of a CTI program, and its role in the context of new regulatory requirements.
What is Cyber Threat Intelligence (CTI)?
Cyber Threat Intelligence combines intelligence practices with cybersecurity. It involves gaining knowledge of current cyber threats to an organization, including the tactics, techniques, and procedures (TTPs) used by attackers. The knowledge is developed within a comprehensive intelligence cycle, adapted from conventional intelligence practices, and lays the foundation for a company’s strategic cybersecurity decisions.
Cyber Threat Intelligence Definition in the Context of Threat Intelligence, Intelligence, and Threat Hunting
Intelligence vs Cyber Threat Intelligence
Intelligence is the process of gathering and analyzing data, including classified information, to gain critical insights. This definition applies to any area where strategic decisions require an understanding of adversaries and threats to a specific entity. The process is deeply rooted in military and governmental institutions, which have refined the concept of the intelligence cycle.
Threat Intelligence vs Cyber Threat Intelligence
The terms Cyber Threat Intelligence and Threat Intelligence are often used interchangeably, although Threat Intelligence is a much broader concept that goes beyond cyber threats. The process of gathering and analyzing information can therefore include threats related, for example, to the organization’s physical security, geopolitical situation or internal risks (insider threat).
Cyber Threat Intelligence vs Threat Hunting
Threat Hunting stands out among these concepts because, unlike CTI and TI, it does not involve intelligence activities. It means proactive search of the organization’s systems to identify current threats and find previously unknown threats. The activities are based on hypotheses that assume attackers have gained access to the company’s infrastructure. The role of the Threat Hunting team is to find evidence that supports one of these hypotheses and detect the attack, enabling the organization to counter threats where security measures have failed. It is important to note, however, that the hypotheses used in Threat Hunting are often based on Cyber Threat Intelligence data.
CTI in Practice: How Does Cyber Threat Intelligence Work
A Cyber Threat Intelligence program can take various forms, depending on your organization’s maturity in threat intelligence.
In its early stages, a CTI program is often unstructured and focused primarily on operational and tactical levels. CTI analysts monitor specific external threat information sources and build an internal database of Indicators of Compromise (IoCs), using, e.g., an open-source instance of the Malware Information Sharing Platform (MISP). Analysts generate initial cyber threat reports, typically in non-standard formats. The primary goal of the program at this stage is to quickly raise the organization’s awareness of the current threat landscape.
More mature CTI programs aim to use the knowledge gained to improve threat detection and response mechanisms. Processes are already largely structured and involve CTI integration with Security Operations Center (SOC) processes. Initial automation mechanisms are developed to correlate IoCs from external data sources with internal security systems. In addition, CTI analysts are becoming more involved with incident response teams and vulnerability management groups.
An advanced, fully mature Cyber Threat Intelligence program becomes an integrated, formalized security component that fully supports SOC, CSIRT, CERT, and vulnerability management teams. CTI analysts focus on profiling threat actors, assessing campaigns, conducting strategic threat analysis, and optimizing existing processes. In most cases, at this stage, you can also see dynamic threat information exchange with similar organizations. The program then becomes a critical element of the organization’s risk management process.
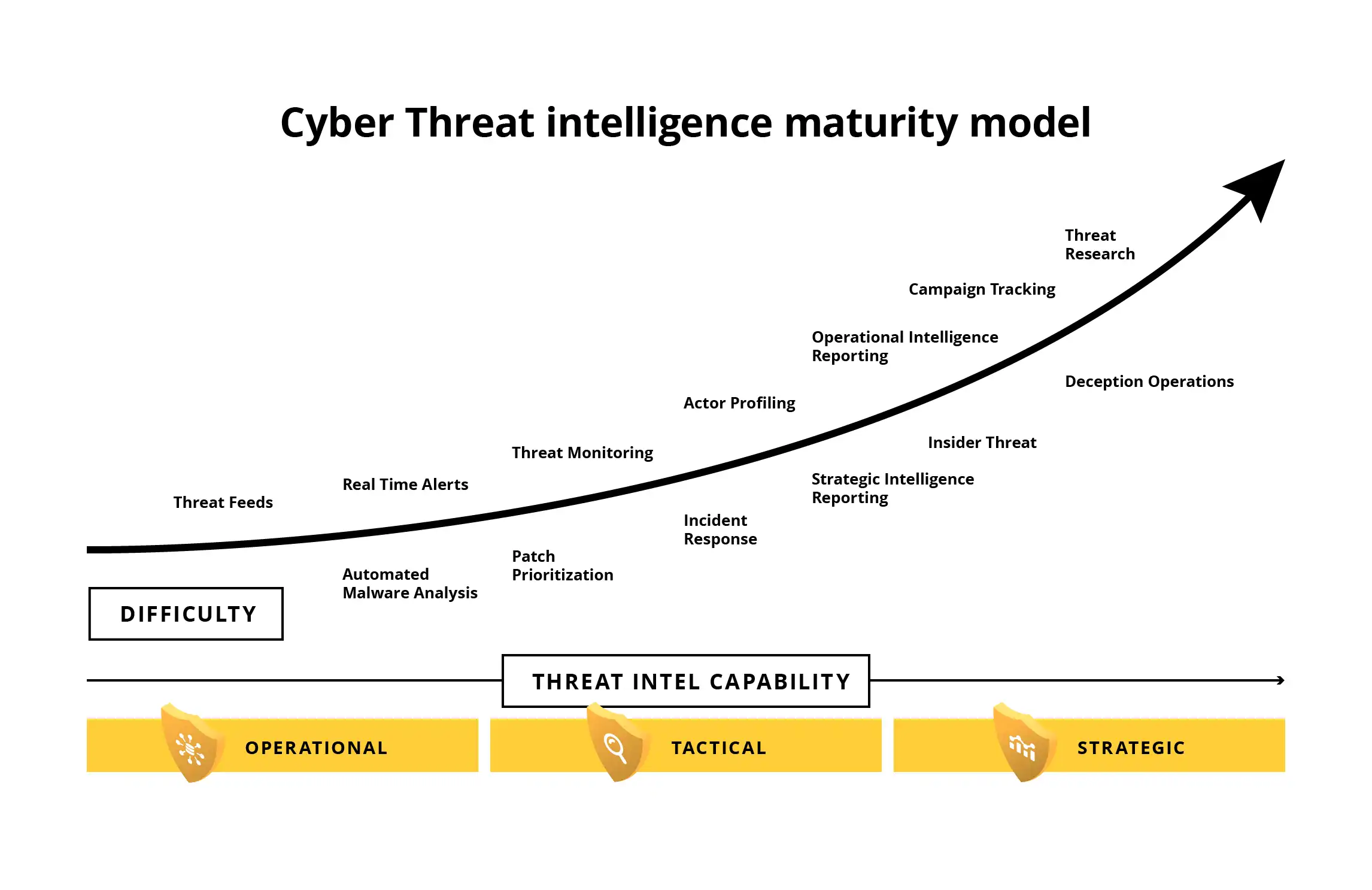
CTI Levels
The end product of a Cyber Threat Intelligence program varies depending on the organization’s needs. CTI usually has three levels:
1. Operational Level
Action: Identifying threat actors, with particular attention to associated Indicators of Compromise (IoCs), malicious file signatures, and attack patterns.
Application: Prioritizing security teams’ detection and responses to identified threats.
2. Tactical Level
Action: Searching for up-to-date technical information on the latest cyberattacks, incidents, vulnerabilities, and exploits.
Application: Identifying and mitigating identified threats using detection rules and security tools.
3. Strategic Level
Action: Providing a bird’s-eye view of the current threat landscape and forecasts for its development.
Application: Providing information to decision-makers to facilitate the development of security strategies, particularly the creation of appropriate policies and procedures and the allocation of appropriate resources.
These levels also represent increasing complexity and depth of analysis. This progression is well illustrated by the Cyber Threat Intelligence maturity model:
When to Implement CTI: 6 Key Aspects
There are several factors that may indicate the need to implement a CTI program in your organization. Here are a few examples:
- Your organization operates in a critical sector. Companies in sectors such as finance, defense, energy, transportation, and healthcare are frequent targets for organized cybercriminal groups. In addition, these industries are often covered by legal regulations mandating the adoption of CTI measures.
- Lack of awareness of threat actors is becoming apparent. Without a good understanding of the current threat landscape, analyzing alerts and assessing organizational risks can lead to mistakes.
- Existing security tools are insufficient. The number of alerts and incidents, coupled with the volume of data being collected, becomes overwhelming and can impede the detection of true threats.
- The organization handles sensitive data. Existing data protection mechanisms become insufficient and require proactive monitoring for potential data leaks.
- Threat prioritization is becoming increasingly difficult. Lack of information may hamper the prioritization of emerging vulnerabilities and threats.
- Your organization is ready for a proactive approach to security. Your reactive approach is no longer adequate, and you need to move to a proactive posture to anticipate and prevent attacks instead of just reacting to them.
Building a Cyber Threat Intelligence Program
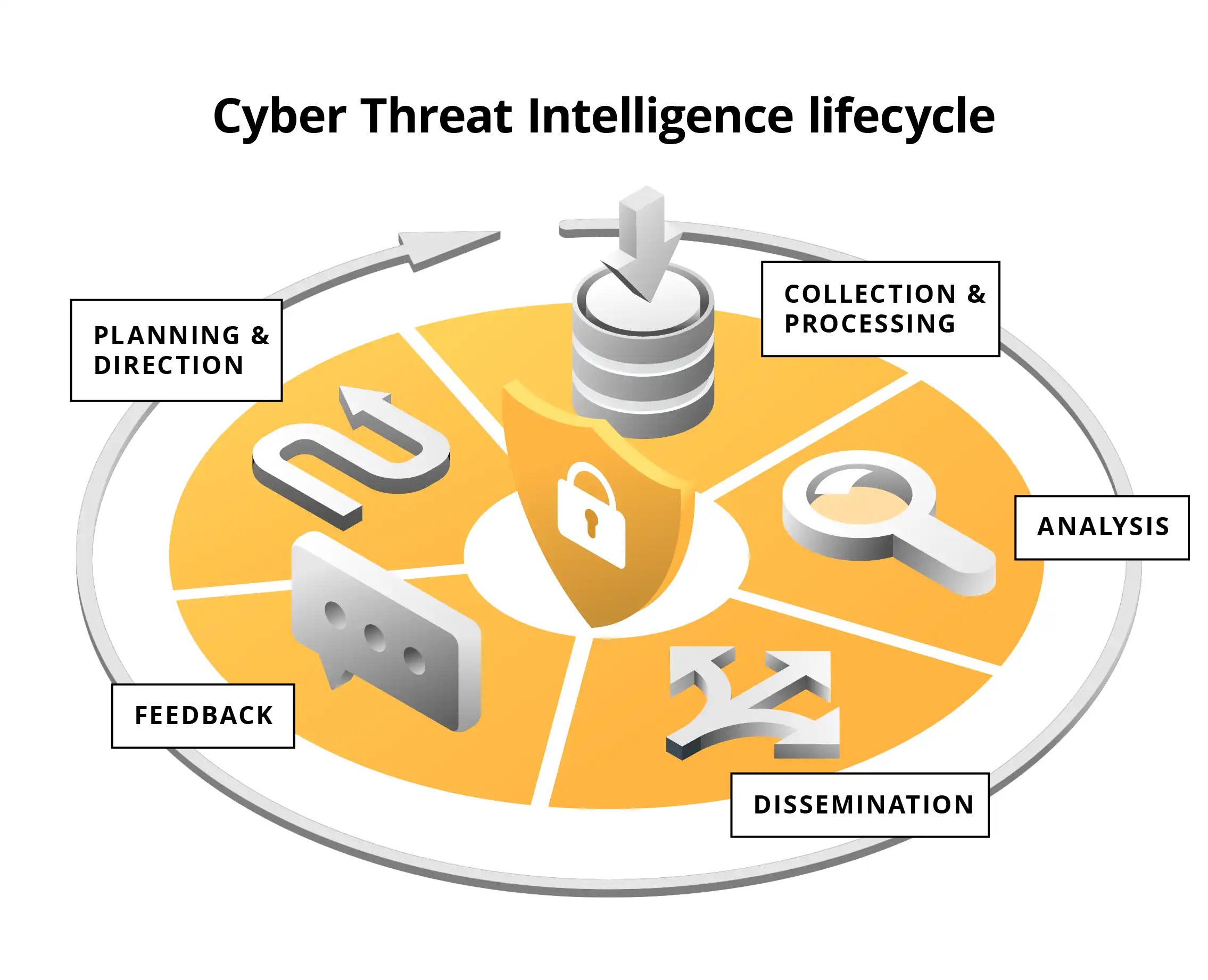
The Cyber Threat Intelligence Lifecycle
In order to properly prepare your organization for the implementation of a Cyber Threat Intelligence program, you should learn about the so-called Cyber Threat Intelligence lifecycle (CTI lifecycle).
The Cyber Threat Intelligence lifecycle is a continuous process of threat information management that includes several key steps: planning, collection and processing, analysis, distribution, and feedback collection.
1. Planning
Defining clear objectives for intelligence activities.
Remember:
- Every objective should be clearly defined and linked to a specific question, problem, or threat.
- The CTI process should lead to security-related decisions for every defined objective. Intelligence requirements that do not meet this condition usually do not add value to the protection of the organization.
- Specify a timeframe for each objective to ensure that information remains useful for a given requirement. Data loses much value if it is not delivered to the recipient in a timely manner that allows the data to influence the organization’s decisions and actions.
2. Collection and Processing
Gathering and processing (e.g., decoding, translation, assessing reliability) raw data from external and internal sources, such as open-source information, Deep web, Dark web, or internal logs.
Remember:
- Prioritize the quality of collected data over quantity—quality is more important for CTI.
- Implement Threat Intelligence platforms (e.g., MISP) to organize and prioritize data effectively.
3. Analysis
Identify patterns, trends, and behaviors of entities that pose threats for the organization, in order to transform data into actionable insights.
Remember:
- Make sure you understand threat actors, including their intentions and capabilities.
- Consider using threat modeling tools, such as those based on the Diamond Model or Cyber Kill Chain. They help structure threat intelligence and provide deeper insight into threat actor activities.
4. Distribution
Share intelligence with appropriate teams and stakeholders, considering the technical level of the recipients.
Remember:
- Ensure the security and ethics of the process, adhering to relevant regulations and data-sharing agreements with third parties.
- Enhance analysis results with visual aids, such as diagrams, charts, or timelines, to improve comprehension.
5. Feedback
Collect feedback and recommendations regarding the insights provided and the entire CTI process. Use these insights to assess and adjust intelligence requirements to the organization’s current needs.
Remember:
- Review the results step-by-step to adapt the process to your organization’s needs as quickly as possible.
- Actively seek feedback. Consider implementing an automated process to collect the data in a structured way.
- Implement metrics that describe the effectiveness of the CTI process, such as changes in response times to threats, the effectiveness of risk mitigation processes, or the fact that a security-related decision was made as a result of the process.
The above cycle applies to intelligence data at each of the previously mentioned levels. It is also important to emphasize that CTI is always an ongoing process that should be tailored to the organization’s needs and objectives.
To ensure that the Cyber Threat Intelligence program is properly tailored to your organization's needs, get expert assistance. Visit our page to learn more about CTI as a Service, the scope of support offered, and the benefits of such a solution.
Cyber Threat Intelligence and Regulatory Requirements
As regulatory requirements continue to evolve, Cyber Threat Intelligence (CTI) plays a critical role in meeting the need to monitor, analyze, and mitigate cyber threats. When used properly, CTI can help organizations not only comply with new regulations, but also improve their operational resilience and the security of their digital infrastructure.
This is illustrated, among others, by the EU Digital Operational Resilience Act (DORA), which entered into force on January 17, 2025. According to Article 13(1) of DORA: “Financial entities shall have in place capabilities and staff to gather information on vulnerabilities and cyber threats, ICT-related incidents, in particular cyber-attacks, and analyze the impact they are likely to have on their digital operational resilience.”
NIS2 Directive also recommends a proactive approach to cyber threats, adding that: “Member States shall ensure that essential and important entities take appropriate and proportionate technical, operational and organizational measures to manage the risks posed to the security of network and information systems which those entities use for their operations or for the provision of their services...” (Article 21(1)).
We have already covered the European Union’s NIS2 Directive on the OChK blog. If you need to organize your knowledge about what NIS2 is, who it applies to, and how it defines obligations of businesses in terms of cloud computing, make sure you read: “Cloud Computing and NIS2 Directive: How to Prepare Your Company for Changes”.
Conclusions
Implementing a CTI program in an organization is a powerful response to the new challenges of strengthening security and building operational resilience, which are becoming increasingly important not only because of new regulations (such as NIS2 and DORA), but also because of the ever-expanding cyber threat landscape.
The benefits of Cyber Threat Intelligence are primarily related to immediate protection, involving detection of threats, responding to potential security incidents, and streamlining the risk management process.
If you're interested in implementing a Cyber Threat Intelligence program in your organization, but you're not sure how to go about it, don't hesitate to contact us for expert assistance. Let us know in the form below!