In a Nutshell
The NIS2 Directive introduces a distinction between essential and important entities, expanding obligations to new sectors and imposing personal liability on management, along with the risk of significant financial penalties. A key requirement is self-assessment and supply chain auditing, forcing companies to verify the security of their ICT providers. Organizations must implement risk management systems and reporting procedures for significant incidents. In a cloud model, compliance is based on shared responsibility and ensuring business continuity through Disaster Recovery and resource redundancy. Meeting monitoring requirements is streamlined by SOC as a Service, while proactive protection is bolstered by Cyber Threat Intelligence processes.
In a time of increasing business reliance on technology, the security of data and systems is becoming a priority for companies worldwide. This is especially true for enterprises in European Union Member States, for which the introduction of the NIS2 Directive brought about a number of new challenges. In this article, we explain what exactly NIS2 involves and which organizations it applies to. We also highlight some of the key aspects to focus on so you can safely continue using cloud computing services while ensuring that your organization complies with the new requirements.
NIS2 in a nutshell, or what you need to know about the Directive
What is NIS2?
NIS2 (Network and Information Systems Directive 2) is an EU Directive primarily aimed at building cybersecurity capabilities across the EU by introducing new obligations for companies in more crucial sectors of the economy.
NIS2 applies to entities that provide services that are essential and important to the EU’s economy and society. In practice, this means that those operating in such sectors will have to implement more stringent security measures than before to protect their systems from cyber threats and meet new regulatory requirements. The provisions of the NIS2 Directive require an amendment to the Polish Act on the National Cybersecurity System (ANCS), which should be applied from October 18, 2024.

Pic. 1: NIS2 Objectives
Who is subject to NIS2 and how does it define corporate obligations?
If you want to determine whether and to what extent NIS2 requirements apply to your organization, you need to pay attention to several important changes.
1. New rules of classification for entities and areas of the economy subject to NIS2
The previous division into essential service operators and digital service providers has been replaced by a classification into essential and important entities. The new Directive introduces areas such as:
- Public administration and space,
- Postal and courier services,
- Waste management,
- Manufacture, production and distribution of chemicals,
- Production, processing and distribution of food,
- Manufacture of medical devices and in vitro diagnostic medical devices,
- Manufacture of computers, electronic and optical products,
- Manufacture of electrical equipment,
- Manufacture of motor vehicles, trailers and semi-trailers,
- Research.
The first area is classified as an essential sector while the others are classified as important sectors. It should also be noted that the current list of entities provided for in the draft ANCS is broader than the set forth directly by NIS2 Directive.
2. Size-cap rule
Generally, companies that qualify as medium-sized enterprises (i.e., those with at least 50 employees and a turnover or a total annual balance sheet result exceeding €10 million) or those that exceed the ceilings for medium-sized enterprises are obliged to comply with NIS2. However, there are exceptions where even small and microenterprises (e.g., where a disruption of the service provided by the entity could have a significant impact on public safety, public security or public health), as well as public sector entities, may be covered by the new regulations.
3. Identical obligations
The fundamental obligations for essential and important entities are very similar, unlike the current regulations that oblige digital service providers to meet cybersecurity requirements to a fairly limited extent.
4. Self-assessment
NIS2 Directive changes the manner of determining whether an entity falls within its scope by introducing a general principle of self-assessment. As a result, entities operating in the said sectors are obliged to verify on their own whether they are subject to NIS2 requirements.
5. The domino effect
Even if an entity is not directly subject to the Directive, it may be part of the supply chain of entities that fall within its scope. Therefore, it should also ensure compliance. This is particularly important for entities using cloud services, as discussed below.
6. Risk management
A review of NIS2 provisions does not provide detailed and clear information on the specific security measures an organization should implement. It merely lists a number of elements that should be taken into account when complying with cybersecurity risk management measures. However, the requirements stipulated by NIS2 have been somewhat clarified in the draft amendment to the ANCS. The bill imposes on entities an obligation to implement an information security management system for processes that affect the provision of services, and indicates the elements such a system should provide.
7. Sanctions
There are heavy financial penalties for failure to implement the requirements. NIS2 sets forth not only administrative penalties of up to €10 million or 2% of the total annual turnover (for essential entities) and €7 million or 1.4% of the total annual turnover (for important entities), but also penalties on individuals. The draft ANCS provides for the possibility of imposing fines on the head of the entity of up to 600% of the salary received by the penalized person.
Implementation of key requirements: where to start
The number of processes and the tools an organization should implement will depend primarily on:
- whether the entity was previously covered by the provisions of the ANCS,
- whether and to what extent the entity has implemented an information security and business continuity management system,
- what level of maturity it represents in the area of cybersecurity.
It is a good idea to begin implementation with a gap analysis/compliance audit that focuses specifically on the processes and assets needed to deliver your services.
In the case of entities in the supply chain (for example, companies using cloud computing services), contractual provisions will be of key importance. Entities covered by NIS2 will expect their suppliers not only to implement specific security measures, but also to ensure they can exercise their audit rights.
It is also important to involve decision-makers in the implementation process, and to provide adequate resources, including competencies and financial resources. The new regulations do not provide a predefined checklist of safeguards that need to be implemented as their selection will depend mainly on risk assessment results and the ability to fulfill legal obligations, especially with regard to incident management.
NIS2 and cloud services
In the context of using cloud computing services, some requirements are particularly relevant. Make sure you pay attention to:
1. Implementation of risk assessment policies
When developing risk assessment policies and then identifying and assessing risks for processes implemented with cloud computing services, consider their characteristics and specific types of risks.
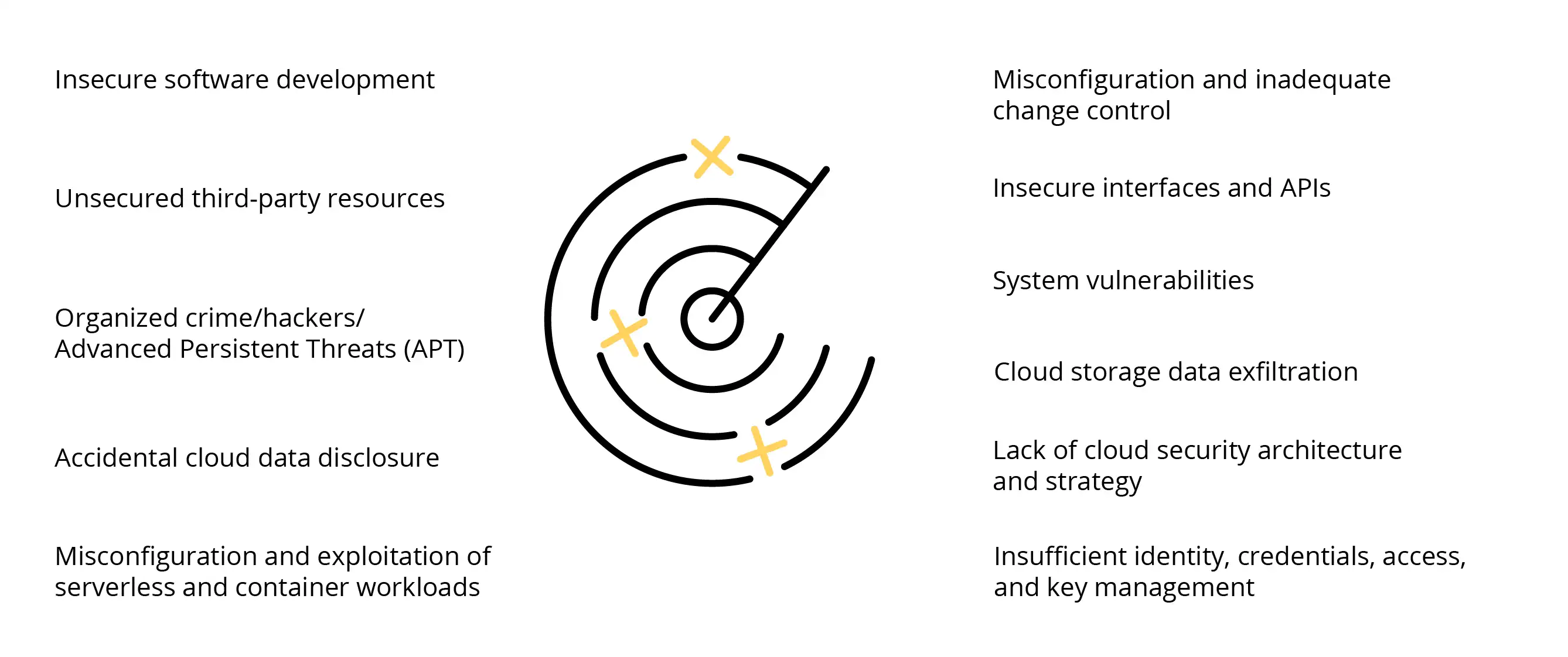
Pic. 2: The most common types of threats to processes implemented using cloud services
The key is to identify the risks, taking into account the rules of shared responsibility. The areas for which the customer and the cloud provider are responsible, respectively, depend on the model of the service provided (usually: IaaS, PaaS and SaaS). This precise division should be your starting point. For more about the shared responsibility model, please read: Cloud Provider Liability: What Are the Available Market Models?
You should also remember that the risk assessment process should be ongoing. Its results and risk management policies should be properly documented and regularly reviewed and updated. The assessment may include not only risks arising from the use of specific systems or technologies but also those related to processes (e.g., those related to ensuring adequate competencies, key personnel, or supply chain).
2. Supply chain security and continuity
In Foresight Cybersecurity Threats for 2030, ENISA predicts that supply chain security breaches will become one of the most likely cyber threats in the coming years. The new regulations address these predictions and oblige entities to manage the risks associated with the providers of products, services and ICT processes on which the provision of services depends.
One way to address these requirements is to implement a supply chain security policy that includes criteria for selecting, verifying, and monitoring suppliers. When evaluating cloud providers, you should consider their reputation as well as other aspects, such as guarantees stipulated in the agreement (e.g., SLAs, audit rights, rules for using subcontractors, failure and incident reporting, ability to reserve capacity), and also security standards implemented by the provider, including its certifications of compliance with international standards and the scope thereof.
For cloud providers, the latter documents are usually publicly available. For example, you can find information about OChK certificates here.
3. Ensuring business continuity
Supply chain security is closely related to the NIS2 requirements for ensuring business continuity.
In the case of cloud computing, you should consider both the failure of a single device and of a specific zone or an entire region. Contingency plans should provide for the loss of control over the information processed and for the interruption of its operation. In line with best practices, entities that use cloud services should also prepare an exit plan, i.e., a document containing the organization’s plan for withdrawal from the service or system, both in planned situations and in an emergency.
One of the main tools that support business continuity is proper backup and backup management. Backup plans should include: relevant RTO and RPO parameters; ensuring completeness and accuracy of backups; keeping backups in secure and separate locations; appropriate physical and logical access controls; procedures for restoring backups, and defining proper retention periods. Backup recovery and redundancy should also be regularly tested and documented.
Cloud services significantly minimize the risks associated with business disruption. Cloud infrastructure enables you to use multiple geographically separate regions, having multiple zones configured within a region ensures uninterrupted operation of the region even if one zone (i.e., an entire data center) is lost. You can also implement architecture that makes solutions resilient to the loss of an entire region – contingency plan can address the need for a disaster recovery production environment.
4. Security monitoring
One of the basic requirements set forth by NIS2 is to ensure an adequate incident management process to detect incidents and minimize their effects and impact on recipients.
In practice, this means implementing mechanisms and tools to prevent and immediately respond to incidents. These tasks can be carried out by a cybersecurity team, i.e., a Security Operations Center, as part of the SOC as a Service, which ensures 24/7 monitoring of IT resources and environments.
NIS2 expands the definition and changes classification criteria for significant incidents. This means that even organizations that have implemented incident management processes compliant with the current regulations should adapt their processes and procedures to the new regulations.
5. Gathering information on cyber threats and vulnerabilities
A modern cybersecurity management strategy should also cover processes that enable a proactive approach to externally emerging threats. This recommendation is fulfilled through the implementation of a Cyber Threat Intelligence process, which involves gathering up-to-date information on threats, attacks and potential adversaries, and providing relevant stakeholders with the information. Of importance in this case is not only collecting information on cyber threats, but also their proper analysis and addressing the risks associated with their potential materialization.
The new regulations introduce requirements for monitoring cyber threats and also provide for the use of proper information exchange channels to raise awareness. Essential and important entities will also be required to notify their users of so-called significant cyber threats and of the potential preventive measures available to users. It is therefore necessary to implement processes that enable proper classification and analysis of cyber threats, along with the necessary communication plans and procedures.
Summary
Preparing your business for the changes introduced by the EU’s NIS2 Directive is essential for maintaining a high level of cybersecurity, ensuring business continuity and data protection of the organizations operating in the core sectors of the economy. The new challenges posed by NIS2 also extend to companies that use cloud computing services. In order to face them, they must undertake some specific steps to strengthen their IT systems.
Making sure your business responds to NIS2 provisions properly may seem a daunting task. However, proper organization of the necessary activities and a proactive approach can benefit your organization not only in terms of ensuring regulatory compliance, but also increased customer trust, enhanced cloud data protection and operational stability, which can contribute to company growth in the long run.