In a Nutshell
The SOC-as-Code model allows for a reduction in Mean Time to Detect (MTTD) and the elimination of manual errors by fully automating SIEM and SOAR systems using Infrastructure as Code (IaC) methodologies. Storing detection rules and playbooks in a Git repository ensures full auditability and version control, while the use of CI/CD pipelines enables automated validation of rule logic and instantaneous deployment of changes to production environments. With this approach, security infrastructure—built on systems such as Microsoft Sentinel—becomes highly scalable, consistent, and reliable, shifting the burden of repetitive configuration tasks away from SOC teams in favor of agile, code-driven defense management.
The concepts of Infrastructure as Code (IaC) and Continuous Integration/Continuous Deployment (CI/CD) are well known and used in many projects, mainly those implemented in the cloud and related to software development. Will they also work on cybersecurity projects? Definitely—especially when implementing and managing SIEM and SOAR systems come into play. In this article, you will find key information on how to use them to manage your Security Operations Center in a modern way.
What are SIEM and SOAR systems?
SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) are some of the most basic tools used by security teams in both small and large organizations, wherever the topic of security monitoring or log analysis arises. SIEM allows you to collect data and, to some extent, automatically analyze it, looking for suspicious patterns and correlations (detection rules), while SOAR allows you to streamline and automate the process of responding to detected threats.
Traditionally, SOC teams manage SIEM and SOAR systems manually, which creates the risk of inconsistencies, human error, and scalability issues. The use of IaC and CI/CD methodologies goes a long way towards solving these problems.
Infrastructure as Code in the context of SOC
Infrastructure as Code in the context of SOC primarily involves storing configuration and infrastructure elements in code, in line with the basic idea of IaC. For SIEM and SOAR systems, in addition to the resources themselves (e.g. the Log Analytic Workspace instance and Microsoft Sentinel stored as Terraform code), you can also collect detection rules, parsers or SOAR playbooks.
This approach can be particularly helpful in a scenario where the code is stored in a version-controlled repository (e.g., Git), further aligning with the idea of SCM (Source Control Management). The repository is then a single, central source of information, where you can easily verify any changes made to resources and/or their configuration.
CI/CD in the SOC management process
Another key element in the modernized SOC management method are CI/CD pipelines. Their implementation can be divided into two parts.
Continuous Integration (CI)
CI involves the development and continuous integration of resources and configurations into a common repository. In order to ensure that the necessary standards are maintained and that both formal and technical requirements are met (e.g., avoiding the introduction of a non-functional/faulty configuration that could expose the system to an unplanned outage), each change can be subjected to automated testing before it enters the production brunch. This additional layer of control allows more SOC team members to work on solutions simultaneously, without the risk of compromising production systems.
Continuous Deployment (CD)
CD involves automatic deployment of configuration changes to SIEM and SOAR systems immediately after passing the tests described above and possible acceptance tests conducted by the SOC engineering team. By structuring the process in this way, any changes, updates, or new rules are introduced into the environment quickly and in a controlled manner.
Key benefits of managing SOC with IaC in combination with CI/CD processes
- Consistency and reliability. Automating the deployment process eliminates the risk of human error and ensures consistency across environments.
- Faster deployment cycles. You can deploy changes and updates quickly, and partially or fully automate the change verification process. This, for example, in the context of introducing new detection rules in a SIEM system, can translate into reduced mean time to detect (MTTD).
- Version control. All changes are tracked and subject to version control. They are also stored in repositories, which allows for full auditing and monitoring of each change, and, if necessary, quick rollback and easier collaboration in large teams.
- Test automation. Integrated testing of new changes in the CI/CD pipeline prevents disruption to existing workflows and can also prevent faulty configurations from being introduced into production environments.
- Scalability. Modernization and automation of the SOC management process will make it easier to scale with the growth of the security infrastructure, and to manage large and multiple environments at once.
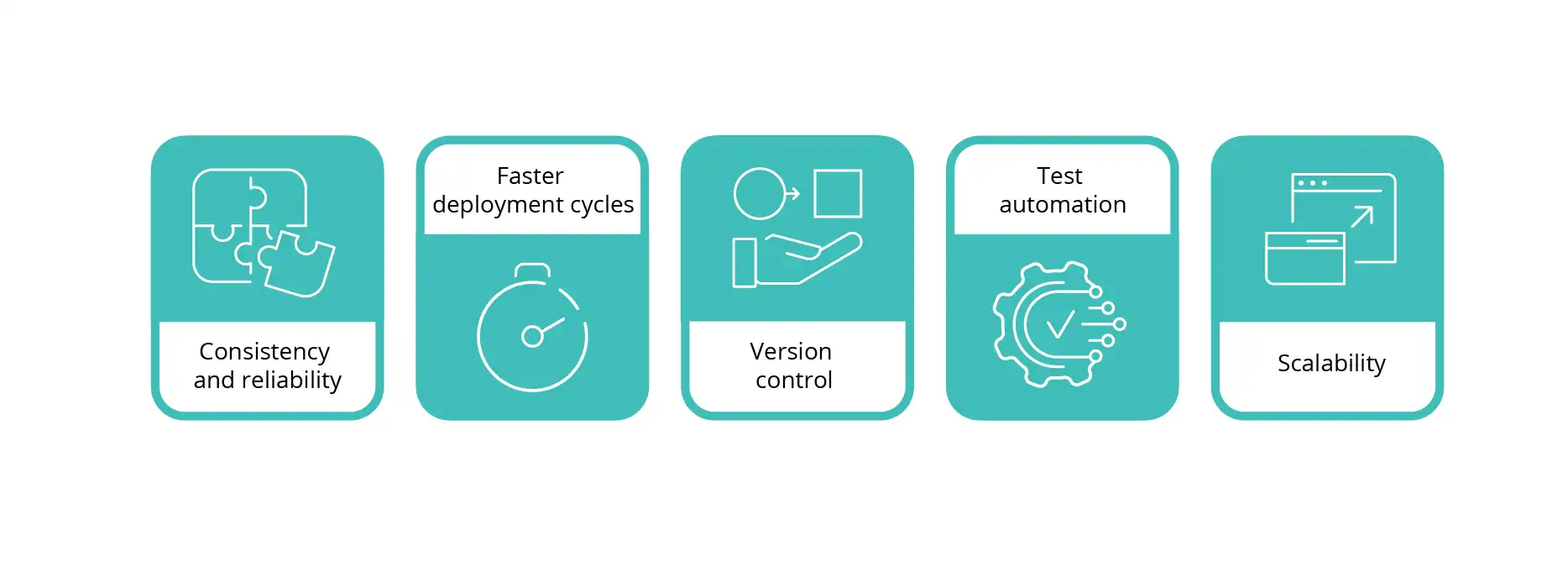
Pic. 1: Key benefits of managing SOC with IaC in combination with CI/CD processes
Sample CI/CD workflow for implementing detection rules in SIEM
The easiest way to quickly understand how the process of combining the ideas of IaC and CI/CD may look like in practice is to present it with a specific example—the SOC team using SIEM (e.g. Microsoft Sentinel) and managing detection rules precisely by using CI/CD processes. In this case, the lifecycle of the implementation and/or adaptation process could be as follows:
1. Source development and control
- Developing new detection rules by analysts from the security team, storing them as code and using a dedicated branch in the Git repository.
- Creating a pull request that starts the automatic pipeline.
2. Automatic validation
- Performing automatic, static code analysis, looking for, e.g., syntax errors.
- Carrying out unit tests to validate the logic of the detection rules.
3. Integration and acceptance
- Deploying new rules to the test environment; running a simulated attack scenario to verify the effectiveness of the rules and ensuring that they do not generate false positives.
4. Production deployment
- Performing additional acceptance tests for changes by engineers from the SOC team (optional).
- Automatically deploying rules to the production environment.
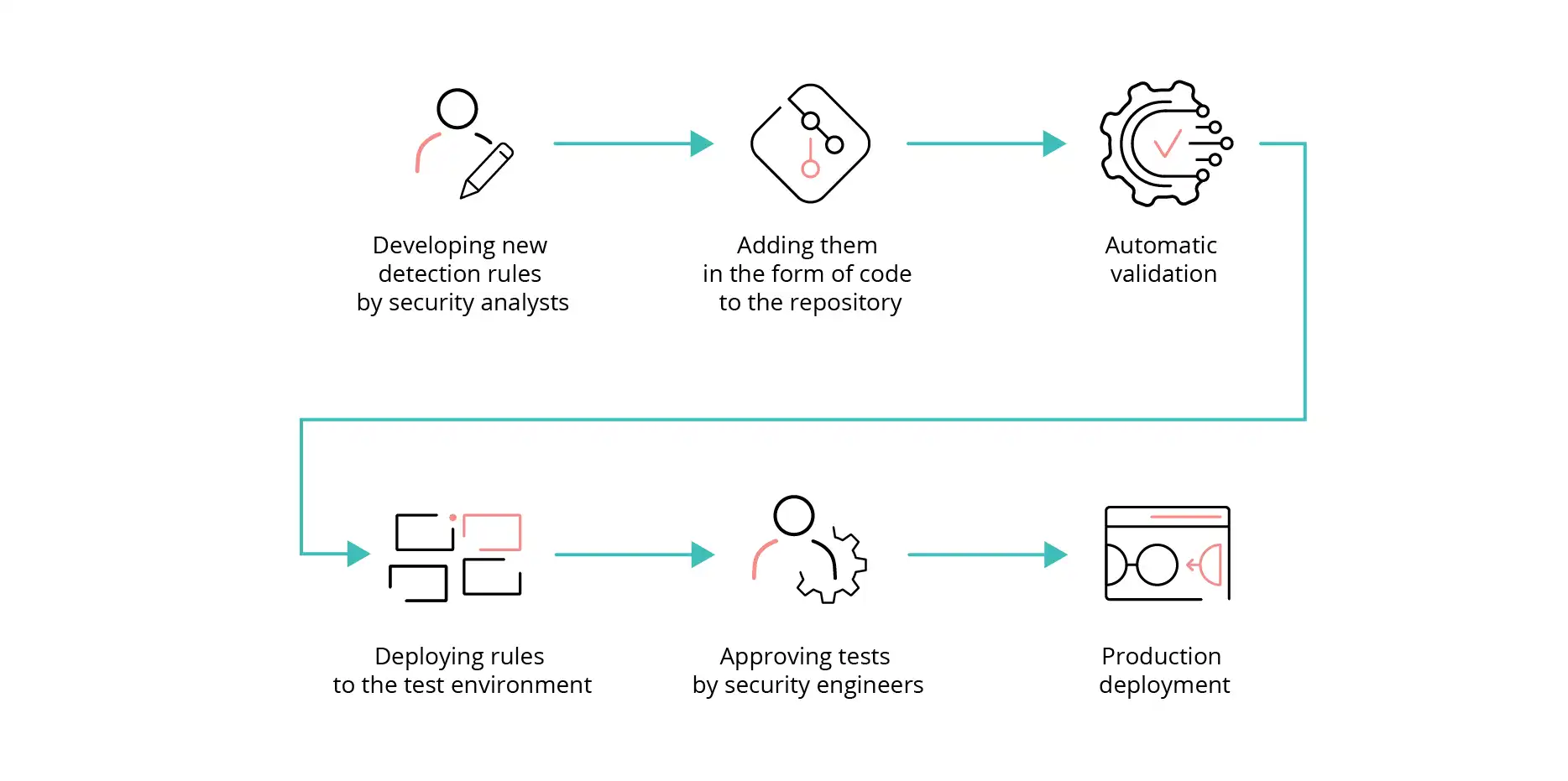
Pic. 2: The example CI/CD workflow for implementing detection rules in SIEM
Summary
SOC as a Code, i.e., managing SOC with IaC and CI/CD processes, primarily increases process reliability, transparency of introduced changes, and scalability of environments, which is particularly noticeable in the case of implementing and maintaining SIEM and SOAR systems. Such an approach also promotes effective team collaboration and eliminates errors typical of manual management, while allowing to monitor the risk of introducing unintended changes into production environments.
Adopting the IaC and CI/CD methodologies is a step towards a significant modernization of the way SOC teams work, enabling them not only to keep pace with the ever-changing cybersecurity/compliance service landscape but also to ensure readiness for future challenges.