In a Nutshell
A Security Operations Center (SOC) is a centralized unit that integrates specialized security analysts, operational processes, and advanced tools to provide 24/7 oversight of an organization’s IT infrastructure. A key dilemma remains the choice between building an in-house SOC and opting for a SOC as a Service (SOCaaS) model. While an internal operation center provides the highest level of independence, it entails high costs and the challenge of recruiting scarce security talent. Conversely, choosing a SOCaaS provider allows for a significant reduction in operational expenses while simultaneously supporting regulatory compliance. The foundation of effective protection lies in core SOC components, such as SIEM systems (e.g., Microsoft Sentinel), proactive threat hunting, SOAR automation, and incident response processes. When selecting an external provider, it is essential to conduct a detailed risk analysis, verifying parameters such as SLAs, ISO 27001 certification, and data protection transparency.
In an era where virtually every organization operates online and data is its most valuable asset, the risk of cyberattacks is higher than ever. This is driven both by cybercriminals' profit motives and the complex geopolitical situation in our region.
The statistics are alarming: according to a Check Point Research report from October 2025, the average number of cyberattacks on organizations in Poland reached 1,772 per week, placing us well above the European average of 1,616 attacks. The financial scale of this problem is also skyrocketing—Sophos reports that in 2024, the average ransom payment was $2 million (up from $400,000 in 2023).
The scale and pace of change in the cybercrime landscape mean that many companies struggle to adapt their security measures to this new reality. This is where the Security Operations Center (SOC)—a centralized hub for fighting threats—comes into play.
After reading this article, you will know:
- what a Security Operations Center is and the key roles within it,
- the difference between an in-house SOC and the SOC-as-a-Service model,
- the functions, components, and key tasks of a SOC,
- which technologies support security operations,
- the biggest challenges of building your own Security Operations Center,
- the primary benefits of implementing SOC-as-a-Service,
- and how to choose the right SOC-as-a-Service provider.
What is a Security Operations Center (SOC) and Why Do You Need It?
A Security Operations Center is the integration of specialized talent, robust processes, and advanced technology. The SOC team's mission is clear: to provide continuous monitoring, detection, and response to security incidents. In today’s landscape, cybersecurity threats are no longer just an IT issue—they are an inseparable component of operational risk that demands proactive management and a well-defined response strategy.
The need for a SOC is also reinforced by the shifting regulatory environment. For example, the upcoming implementation of the EU's NIS2 Directive mandates that covered entities maintain constant oversight of their digital security.
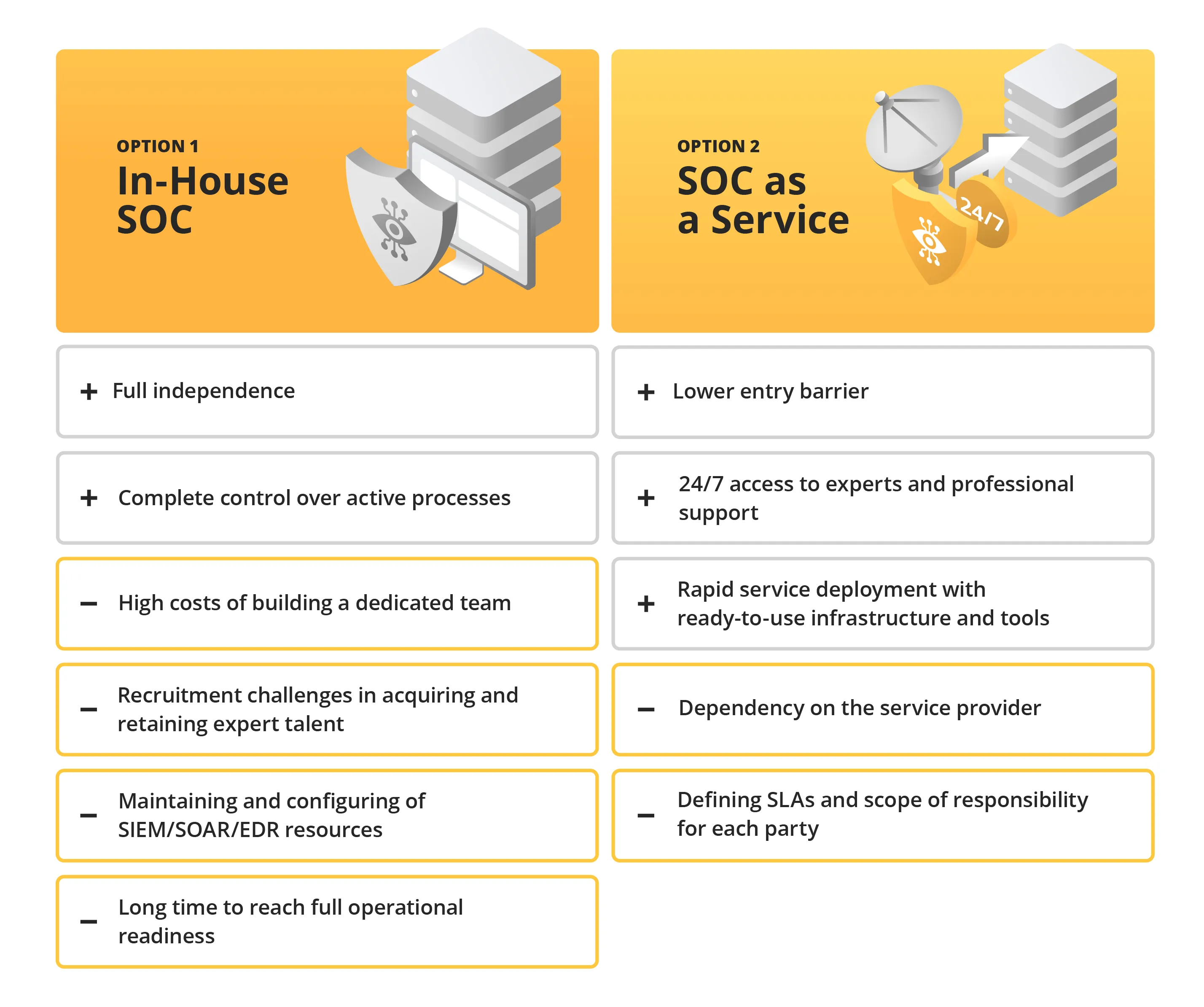
Ultimately, most organizations face a strategic choice that will define their resilience for years to come: should they build an internal security team from the ground up, or leverage a SOC-as-a-Service (SOCaaS) model to tap into external expertise?
How to Build a Security Operations Center? The Reality Check
Before deciding which path is right for you, it is important to understand what building a Security Operations Center actually entails in practice.
The Talent Stack: Who Runs a SOC?
A SOC isn't just about hiring a "security specialist." It requires a variety of distinct roles that are not only expensive to maintain but also increasingly difficult to find in today’s competitive job market. A typical SOC team consists of experts such as:
- Security Analysts (L1/L2/L3): Responsible for the continuous analysis of alerts, event correlation, and the escalation of security incidents.
- Incident Response Specialist: A person who takes the lead and quickly reacts when an incident occurs.
- Cyber Threat Hunter: A proactive expert who searches for sophisticated threats that might bypass automated detection rules.
- Security & SIEM Engineer: Responsible for maintaining, developing, and integrating the organization's security tools.
- SOC Manager/Lead: A person responsible for processes, people, reporting, and communication with the business.
To ensure real support and operational continuity—while accounting for vacations, sick leave, and staff turnover—even a mid-sized organization often needs a team of a dozen or more specialists to remain effective.
Technology and Infrastructure: The Costly Foundation of Cybersecurity
Parallel to building a team, it is necessary to deploy and maintain a comprehensive technology stack. This typically includes SIEM, EDR/XDR, and Security Orchestration, Automation, and Response (SOAR) systems (e.g., Microsoft Defender, Microsoft Sentinel, or Google SecOps). Beyond the initial setup, this requires:
- continuous administration and fine-tuning of detection rules,
- regular updates to Threat Intelligence feeds,
- ongoing testing of attack and response scenarios,
- ensuring high availability and infrastructure resilience.
These are not one-time implementations, but rather ongoing operating expenses that grow alongside the organization and the number of integrated systems.
HR Challenges and Team Retention
One of the most difficult aspects of managing a SOC is staff retention. SOC analysts thrive on professional growth—they want to work with diverse, advanced cases and stay ahead of new attack techniques. Ironically, in a well-secured organization, the number of highly complex technical incidents—the kind that truly challenge security experts—tends to be low. This creates a classic operational paradox: the more mature the environment, the fewer advanced incidents there are to analyze, which can lead to lower long-term motivation and higher turnover. Keeping a team motivated requires significant investment in training, certifications, and time—resources that are often in short supply in a 24/7 operational environment.
Is Building Your Own SOC Team Worth It?
The short answer is: it depends. While building an in-house SOC is possible, in practice, it is one of the most demanding cybersecurity initiatives an organization can undertake. On the surface, it may seem like a straightforward three-stage process—hiring a few specialists, deploying tools, and launching monitoring. In reality, it is a multi-front challenge involving:
- Technology: Implementing and, more importantly, maintaining tools that require constant tuning to keep up with evolving cybercriminal tactics.
- Processes and Procedures: Defining incident response playbooks, escalation paths, event classification, vulnerability management, reporting, and ensuring compliance with regulations (such as NIS2, DORA, and GDPR).
- Expertise: Building a multi-person team (including the L1-L3, Incident Response, and Threat Hunter roles mentioned earlier) and providing 24/7/365 coverage—accounting for vacations and sick leave. At current market rates, this can cost millions of dollars annually.
- Competency and Growth: Continuous training, certifications, testing (such as purple teaming and tabletop exercises), and staying current with the latest attack vectors.
- Cross-Team Collaboration: Facilitating close cooperation not only with IT departments but also with business units, executive leadership, compliance, and Data Protection Officers (DPO).
An internal SOC offers the highest level of independence. However, due to its complexity and cost, it is generally recommended for large, mature organizations that are ready to sustain these significant financial and operational commitments. For many, the barrier to entry is disproportionate to the actual business benefits.
If this sounds like an overwhelming path for your organization, this is where the conversation about alternatives begins.
SOC-as-a-Service: Definition, Functions, and Key Components
For many organizations—especially those without mature security structures—a practical alternative is to outsource monitoring and response to a specialized SOC-as-a-Service (SOCaaS) provider.
What is SOC-as-a-Service (SOCaaS)?
SOC-as-a-Service involves entrusting the core aspects of an organization’s IT security to an external company that specializes in incident management. In this model, the partnership is governed by a service agreement where the provider handles threat monitoring, analysis, and incident response—or supports the organization in managing them based on mutual arrangements—all on a 24/7 basis. Given the sensitive nature of this collaboration, full trust and proactive support in problem-solving are essential.
Key Functions of SOC-as-a-Service
SOC-as-a-Service is more than just standard security outsourcing; it is a continuous shield protecting the organization from real-world threats. Experts operate 24/7, relentlessly monitoring the IT infrastructure and responding to incidents the moment they arise, before they can escalate into a major crisis.
SOCaaS leverages up-to-date Threat Intelligence to detect new attack techniques and vulnerabilities before they can be exploited against the company. When an incident occurs, the SOC team does more than just identify it—they assist in remediation and help restore systems to normal operations.
Additionally, SOCaaS helps organizations meet regulatory requirements, such as NIS2 or DORA, by ensuring event monitoring and providing necessary reports and evidence of compliance. The entire process is enhanced by automation, which accelerates response times and increases effectiveness—all without the need to build a costly internal team.
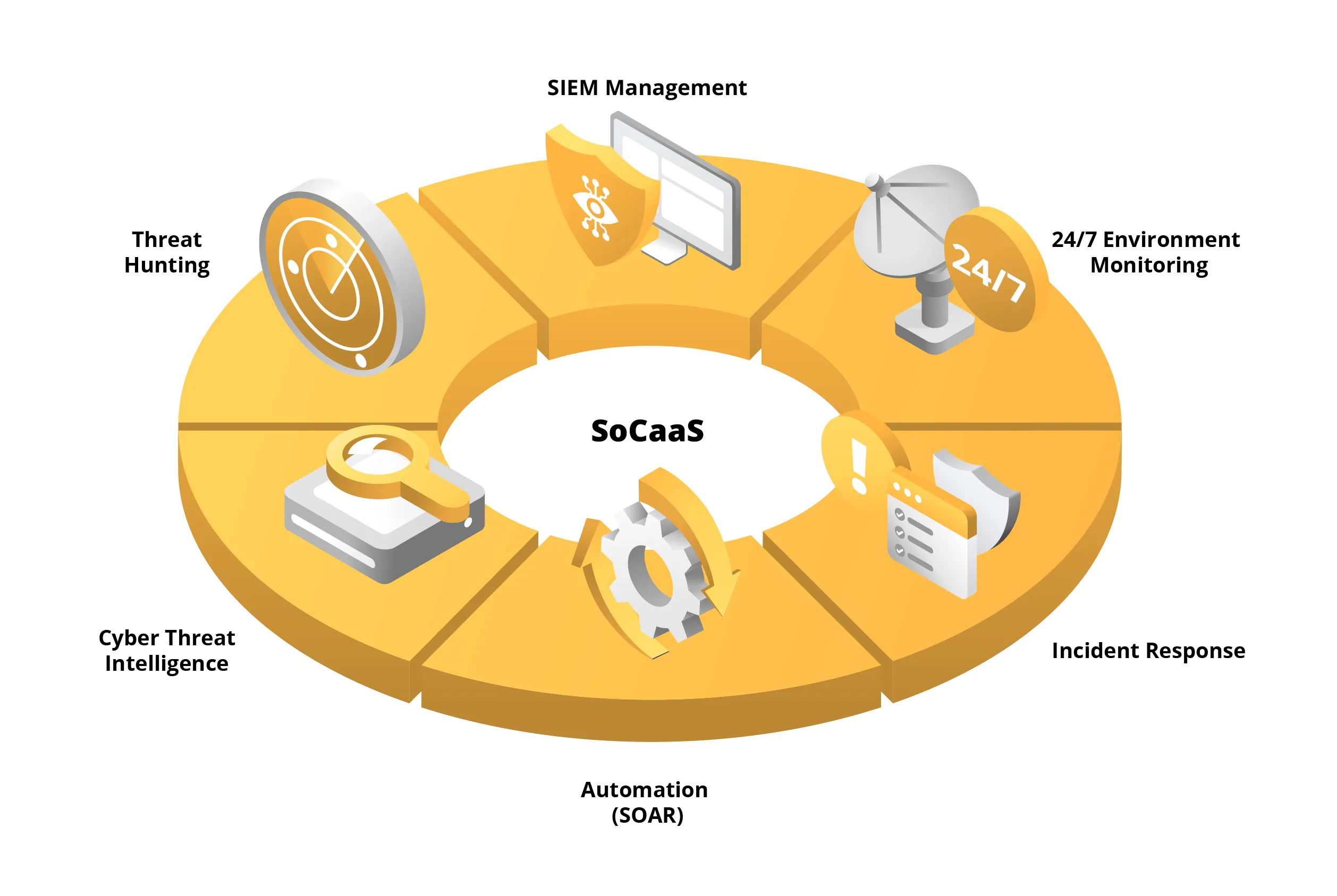
Key Components of SOC-as-a-Service
SOC-as-a-Service is a cornerstone of an organization's cybersecurity strategy. It integrates several critical elements to provide robust protection against cyberattacks—combining the right technology with a strategic approach that allows you to maintain full control over your security posture.
SIEM (Security Information and Event Management)
A fundamental pillar of SOC-as-a-Service is SIEM, an advanced tool used for real-time log analysis and threat detection. With Managed SIEM, your systems are monitored 24/7, allowing the team to identify potential threats before they escalate into serious issues.
Incident Response
When a threat is detected, speed and effectiveness are paramount. SOC-as-a-Service provides advanced detection and response mechanisms through a formal Incident Response process. This includes identifying, managing, and neutralizing threats to minimize damage and ensure a swift return to normal operations.
SOCaaS Continuous Monitoring
Constant oversight of your IT infrastructure is another vital component. SOCaaS provides non-stop monitoring, enabling real-time detection and response. This ensures your systems are protected around the clock, giving you the peace of mind that your environment is never unwatched.
SOCaaS Threat Intelligence
Equally important is Threat Intelligence. This function focuses on collecting and analyzing data regarding the global threat landscape to identify emerging attack patterns and vulnerabilities. It allows you to adapt your security strategy to evolving conditions, ensuring you stay one step ahead of potential attackers.
Threat Hunting
A SOC team serving multiple clients has a much broader perspective on the threat landscape than a typical internal IT department. First, by drawing on experience across various industries, these specialists are significantly more effective at identifying complex attacks. Second, they can employ Threat Hunting—a proactive search for cyber threats fueled by Threat Intelligence. This approach allows them to uncover hidden risks that standard automated tools might miss, eliminating threats before they cause irreversible damage.
Benefits of Implementing SOC-as-a-Service
Reduction in Operating Costs
One of the most significant advantages of SOC-as-a-Service is the ability to substantially reduce operating expenses. Maintaining an internal SOC involves high expenditures on personnel, technology, hardware, licenses, and continuous training. SOC-as-a-Service allows organizations to bypass these heavy investments by leveraging external expertise—an especially attractive proposition for small and medium-sized enterprises.
Flexibility and Scalability
As an organization grows, its security needs evolve. SOC-as-a-Service offers the flexibility and scalability required to adjust the scope of security operations as requirements change. This allows you to easily:
- scale service levels up or down based on current needs,
- avoid additional capital investments in infrastructure,
- maintain peak operational efficiency.
Supporting Regulatory Compliance
Meeting the requirements of regulations such as GDPR, NIS2, or DORA is mandatory for many organizations. SOC-as-a-Service supports companies in this area by providing continuous monitoring and protection of the IT environment. With a team of experts managing 24/7 oversight and implementing procedures aligned with legal mandates, you can ensure your infrastructure remains compliant, helping you avoid potential penalties and legal complications.
Automation of Security Processes
Automation is another key element of SOC-as-a-Service that significantly boosts operational efficiency. By automating monitoring and threat response processes, you can:
- detect threats faster,
- neutralize potential attacks more effectively,
- minimize the risks associated with cyber threats.
In the face of growing cybersecurity challenges, automation has become an indispensable tool. The faster you respond, the more secure your organization becomes.
Access to Expertise and Technology
SOC-as-a-Service provides immediate access to experts and modern tools designed for high-level monitoring and response. While smaller organizations often lack the resources to hire full-time specialists, external providers deliver deep expertise and advanced tools, such as Security Orchestration, Automation, and Response (SOAR) and real-time threat analysis.
SOC-as-a-Service: What You Need to Know Before Choosing a Provider
The decision to entrust your security monitoring to an external partner should be preceded by a thorough risk analysis. Below are three critical aspects every organization should verify before selecting a provider.
1. Regulatory Risks and Compliance
Ensure that the service will genuinely support your organization in meeting legal requirements and that the provider maintains a high level of security—for example, by implementing standards such as ISO 27001. A lack of compliance or failure to secure the supply chain can lead to severe financial consequences and regulatory penalties.
2. Vendor Dependency
Choosing SOC-as-a-Service will, to some extent, create a dependency on an external provider. Because of this, it is vital to carefully verify the SLA (Service Level Agreement) and the scope of liability, both of which define the provider's expectations and performance standards. You should also conduct regular audits of their services or verify that the provider performs such audits independently. Another essential element is a clear Terms of Service (ToS), outlining all critical factors that affect the delivery of the digital service.
3. Data Protection – Potential Risks
Transferring logs to an external entity requires full transparency and the use of advanced security measures. Make sure the provider employs robust data protection protocols to minimize the risk of unauthorized access. It is also worth considering cloud-based solutions that allow you to use SOC-as-a-Service without the need to export data outside your organization’s own infrastructure.
Summary
Building an effective, in-house Security Operations Center is a strategic undertaking that requires significant capital and continuous investment in both people and technology. The key to making the right decision lies in evaluating two main factors:
- Is your organization prepared to cover high upfront and ongoing costs?
- Do you have the capacity to recruit, retain, and train high-level specialists for a 24/7 operation?
If, after analyzing these requirements, your goal is to minimize operational risk, lower the barrier to entry, and gain immediate access to an experienced team and proven technology, the SOC-as-a-Service model may be the right solution for you. By outsourcing your SOC, you can respond rapidly to emerging threats and adapt your security strategy to an ever-changing landscape.
We would be happy to conduct a preliminary needs assessment for your organization to help you determine which path—an internal SOC or a SOCaaS model—is best for your business. Contact us using the form below!
Glossary
Security Operations Center (SOC)
A SOC (Security Operations Center) is a centralized organizational unit, consisting of a team of specialists, technology, and processes, whose main task is continuous monitoring, detection, analysis, and response to security incidents and cyber threats in real time. The SOC acts as the organization's first line of defense, utilizing tools such as SIEM, EDR, and XDR to maintain the overall security posture of the infrastructure.
SOC as a Service (SOCaaS)
SOC as a Service (SOCaaS) is a subscription-based security model where an external provider (such as OChK) delivers the full functionality of a Security Operations Center (SOC) without the need for the client to build their own costly internal infrastructure. This service includes 24/7 monitoring, real-time threat detection and analysis, and incident response support provided by a team of certified security engineers.
System SIEM (Security Information and Event Management)
SIEM (Security Information and Event Management) is a platform that collects, aggregates, and analyzes logs and security events from various sources (servers, applications, firewalls, IDS/IPS systems) in real time. It is the heart of every SOC (Security Operations Center) team.
SOAR (Security Orchestration, Automation and Response)
SOAR (Security Orchestration, Automation and Response) is a set of tools and technologies that automate security incident response processes. SOAR works in close integration with a SIEM platform, enabling faster and more consistent incident management through automated data collection and predefined response scenarios (playbooks).
Threat Intelligence
Threat Intelligence is a proactive process of gathering, processing, and analyzing data about current and future digital threats, hacking groups, and their motivations. This service provides organizations with deep operational context by identifying Indicators of Compromise (IoC) and the Tactics, Techniques, and Procedures (TTP) used by cybercriminals.
Threat Hunting
Threat Hunting is a proactive and iterative process in which security analysts actively search (hunt) within networks and systems for previously unidentified or hidden threats that have escaped automated tools. It is an advanced service within OChK's Cyber Threat Intelligence as a Service, allowing for the detection of complex, targeted attacks.
Incident Response
Incident Response is a structured and integrated process for an organization to handle IT security breaches or successful cyberattacks. It covers the full incident lifecycle from detection to recovery, aiming to reduce financial and reputational losses while ensuring business continuity (BCP) and compliance with regulations like NIS2 or DORA.
ISO 27001
ISO/IEC 27001 certification is a globally recognized standard specifying requirements for Information Security Management Systems (ISMS), the effective implementation of which confirms that an organization applies best practices in the area of information security.
NIS2
NIS2 is a European Union directive that aims to raise the overall level of cybersecurity in member states by introducing new obligations for companies in further key and important sectors of the economy.
DORA
DORA (Digital Operational Resilience Act) is an EU regulation aimed at enhancing the operational resilience of the financial sector against ICT-related disruptions. It establishes harmonized requirements for risk management, incident reporting, and digital resilience testing, including monitoring of external providers like cloud services.


