Ensuring robust security and efficient access management is pivotal for the success of any cloud-based project. For applications running in Kubernetes clusters such as Google Kubernetes Engine (GKE), establishing secure communication with Google Cloud services can be challenging. Traditional methods, which rely on service account key files, run the risk of exposing sensitive data and involve complex configuration and security processes. In addition, using the service accounts associated with GKE nodes does not allow for granular control of access to services. Fortunately, there is a solution that simplifies this process while improving security, called Workload Identity Federation. From this article you will learn what Workload Identity Federation in GKE entails, how it works, and what benefits it brings. You will also understand how it integrates with the entire Google Cloud Platform ecosystem.
How Workload Identity Federation Works in Google Kubernetes Engine
Workload Identity Federation uses identity federation principles to map a Kubernetes workload directly to an IAM (Identity and Access Management) service account.
This approach, recommended by Google Cloud for GKE clusters, enables containerized applications to authenticate with Google Cloud services without the need to manage, store, or distribute key files, thus reducing attack surface and simplifying permission management.
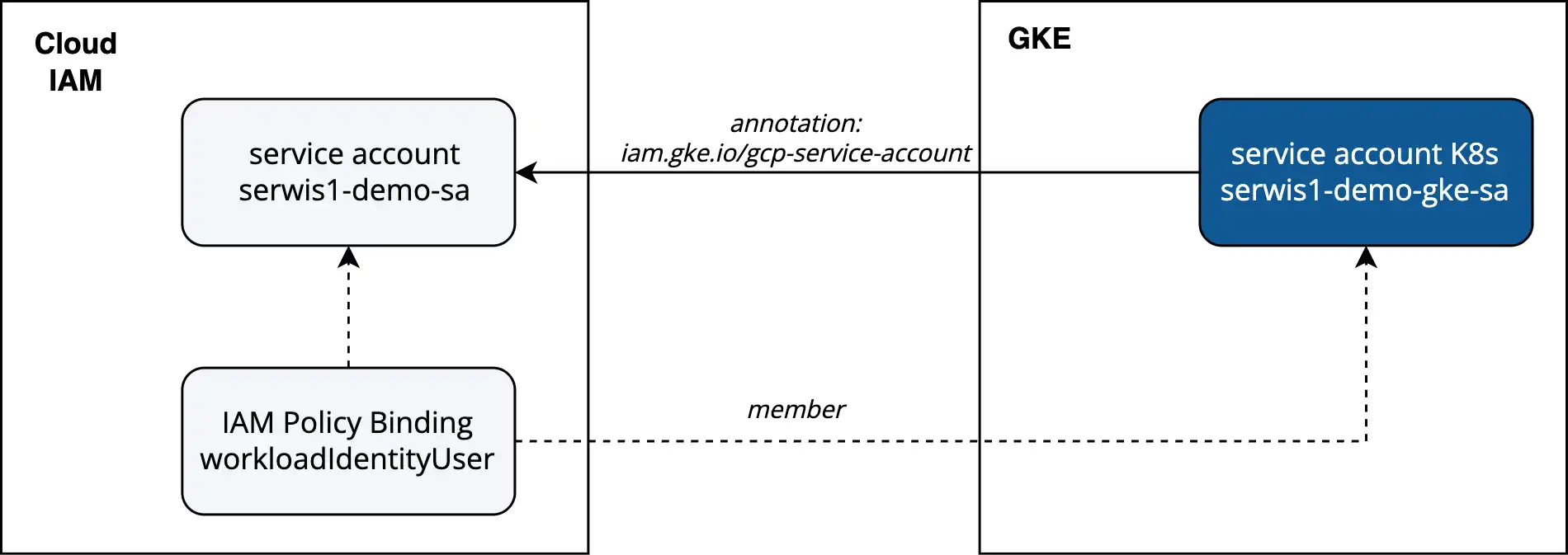
Fig. 1: Relationship between a service account in GKE and Google Cloud Platform
The process of Workload Identity Federation involves several key steps:
- Access Token Request. A containerized application uses the Google Cloud client library to request an access token from the GKE metadata server.
- Kubernetes Authentication. The GKE metadata server verifies the application’s identity by requesting a Kubernetes Service Account (KSA) token from the Kubernetes API server. The token is a digital signature that confirms the application’s identity in the cluster.
- Token exchange. With the KSA token present, the GKE metadata server contacts Google Cloud’s Security Token Service (STS) to exchange the Kubernetes token for a short-lived Google Cloud access token.
- Access to Google Cloud Services. The application, holding the access token, can now interact with authorized Google Cloud services based on its assigned permissions.
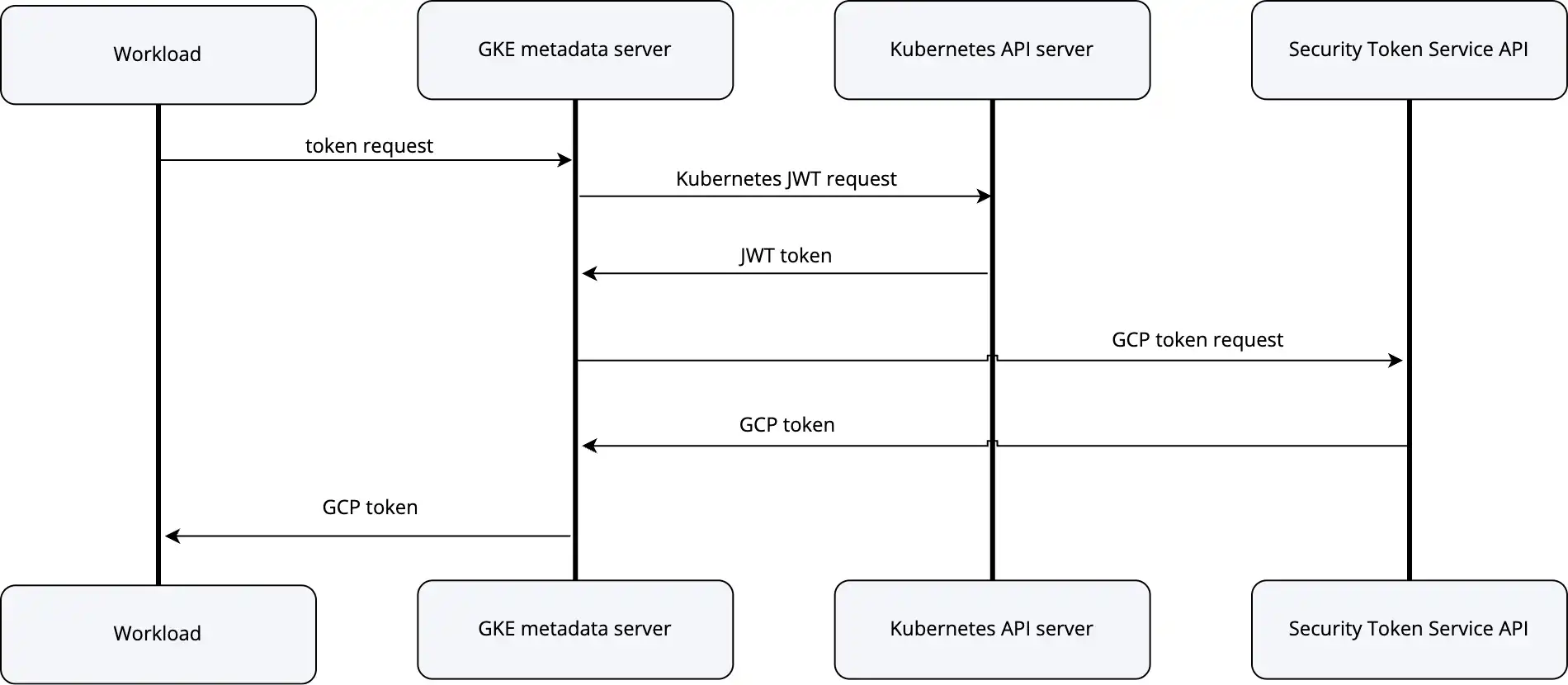
Fig. 2: Authentication flow chart
Workload Identity Federation in GKE offers a secure and efficient method for authenticating applications with Google Cloud services. This eliminates potentially vulnerable key files, and uses existing Kubernetes infrastructure and the Security Token Service to generate temporary access tokens instead. Thus, containerized applications can seamlessly access cloud resources, while administrators enjoy enhanced control over security and permissions.
Key Benefits of Workload Identity Federation
Workload Identity Federation for Google Kubernetes Engine (GKE) offers a robust alternative to conventional authentication methods, with a number of benefits. These are related to security, efficiency, and scalability for cloud-based applications. Key benefits include:
- Improved Security. Eliminating the necessity to manage service account key files significantly reduces the risk of confidential data exposure. When keys are no longer stored in the source code, repositories or cluster configurations, the attack surface is minimized, making unauthorized access to cloud resources more difficult. In addition, the access tokens generated by the Security Token Service further enhance security by limiting the time for a potential attacker to use a compromised token.
- Simplified Management. Workload Identity Federation simplifies the configuration and management of access to Google Cloud services. You no longer need to generate, distribute, or rotate keys, which reduces the administrative burden and allows DevOps teams to focus on application development. Integration with Kubernetes Service Accounts facilitates permission management by leveraging the cluster’s existing access control mechanisms.
- Improved Scalability. Workload Identity Federation is highly effective in dynamic cloud environments where the number of applications and services is constantly evolving. Automating the authentication process makes it easier to scale applications and manage access across distributed Kubernetes clusters. Eliminating the need for manual key configuration accelerates the deployment of new services and improves development workflows.
- Alignment with Best Security Practices. Workload Identity Federation applies the principle of least privilege by enabling precise definition of cloud resource access at the individual application level. Each application is given only the permissions it needs to operate, minimising the risk of unauthorised access in the event of a security breach.
Possible Applications
Workload Identity Federation for GKE can be used in a variety of scenarios to help applications running in a cluster access different Google Cloud services. Here are some real-world examples that illustrate the benefits.
Accessing Cloud Storage
Consider an application in Google Kubernetes Engine that processes data and stores the results in Google Cloud Storage. With Workload Identity Federation, the application can authenticate to Cloud Storage without using key files. All you need to do is provide the Kubernetes service account used by the application with the appropriate permissions to write data to the selected Cloud Storage service. This eliminates the need to manage and store service account keys, improving security and simplifying the overall configuration.
Interactions with BigQuery
Data analysis applications can use Workload Identity Federation to authenticate with BigQuery and execute queries. In such cases, the Kubernetes service account requires read permissions for specific tables or datasets within BigQuery, allowing the application to execute queries directly without storing credentials in the configuration.
Use of Cloud SQL
Applications requiring access to Cloud SQL databases can also benefit from Workload Identity Federation. With the necessary permissions configured for your Kubernetes service account, the applications can connect to the database without exposing passwords or other sensitive information.
Publishing Messages to Cloud Pub/Sub
In event-driven architectures, GKE applications can publish messages to Cloud Pub/Sub. Workload Identity Federation simplifies the authentication process, allowing applications to publish messages without having to manage API keys.
Summary
Workload Identity Federation in Google Kubernetes Engine (GKE) is a powerful tool that transforms the way applications running in Kubernetes clusters access Google Cloud services. By eliminating the need to manage service account key files, it significantly improves security, simplifies configuration, and makes it easier to scale applications. Integration with Kubernetes Service Accounts makes permission management more transparent and efficient, allowing DevOps teams to focus on application development rather than implementing complex security configurations.
Workload Identity Federation works seamlessly with cloud environments where security, automation, and scalability are critical. At OChK, we use this mechanism for a variety of projects. If you need assistance with its implementation and optimization, feel free to contact us.