As the trend towards remote working has become a global reality and cloud technologies have grown in popularity, more and more organizations are choosing to implement Modern Workplace solutions. It means better teamwork and managing the IT environment more effectively, while maintaining a high level of security. In this article, you will learn how to properly secure your workplace and strengthen your company's protection against cyber attacks.
What is Modern Workplace?
Modern Workplace is a dynamic, digitally connected work environment that leverages advanced technology to enhance collaboration, productivity, and security. The solution is based on tools that give users easy access to key data and applications, enabling them to work from anywhere, at any time. This flexibility meets the needs of today's employees and organizations, regardless of their size or industry—it can be implemented for both individual positions in SMEs as well as for thousands of employees spread across offices around the globe in large enterprises.
Employees as the first line of defense against cyber attacks
It goes without saying that employees are the first line of defense against the growing number of cyber attacks. A significant number of the real threats to organizations directly affect the user space (for example, phishing attacks or ransomware). It also happens that employees themselves, more or less consciously, create conditions favorable to cyber criminals through the lack of knowledge or carelessness in applying good security practices and policies, exposing the company to data loss and financial damage. Educating your people and maintaining knowledge in this area is therefore key to ensuring the security of your organization. But it is just as important to take action in the context of the technology you use. This, when properly secured, will provide an effective layer of protection. Below you will find a few examples of solutions that can help you achieve this goal.
How Can You Protect Your Business from Cyber Attacks? 7 Ways to Secure the Modern Workplace
1. Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is one of the key security elements of the Modern Workplace. It requires users to verify their identity using at least two independent methods, so that if a password is stolen, unauthorized individuals cannot access an account without an additional factor, such as a code from an authentication application, a hardware token, or biometrics. According to the study published in the Microsoft Digital Defense Report 2023, implementing MFA reduces the risk of security breaches by 99.2%, significantly decreasing the effectiveness of attacks that rely on password cracking.
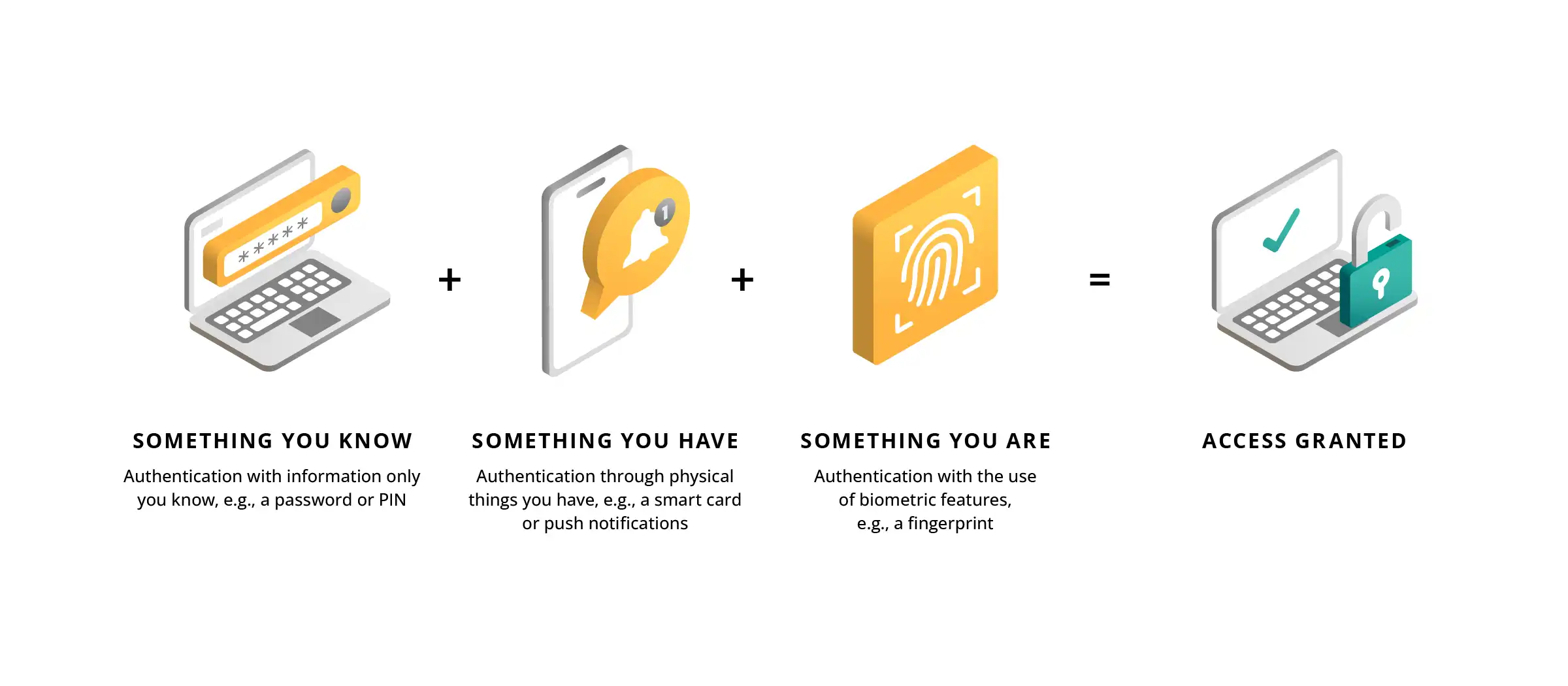
Fig. 1: What is MFA?
To increase your protection, consider at least basic MFA methods for all users. Conversely, for those who have access to sensitive data or administrative privileges, use methods such as FIDO2 keys or passkeys. These are completely phishing-proof and do not require manual code entry, as with SMS codes or codes generated by authentication applications (OTPs).
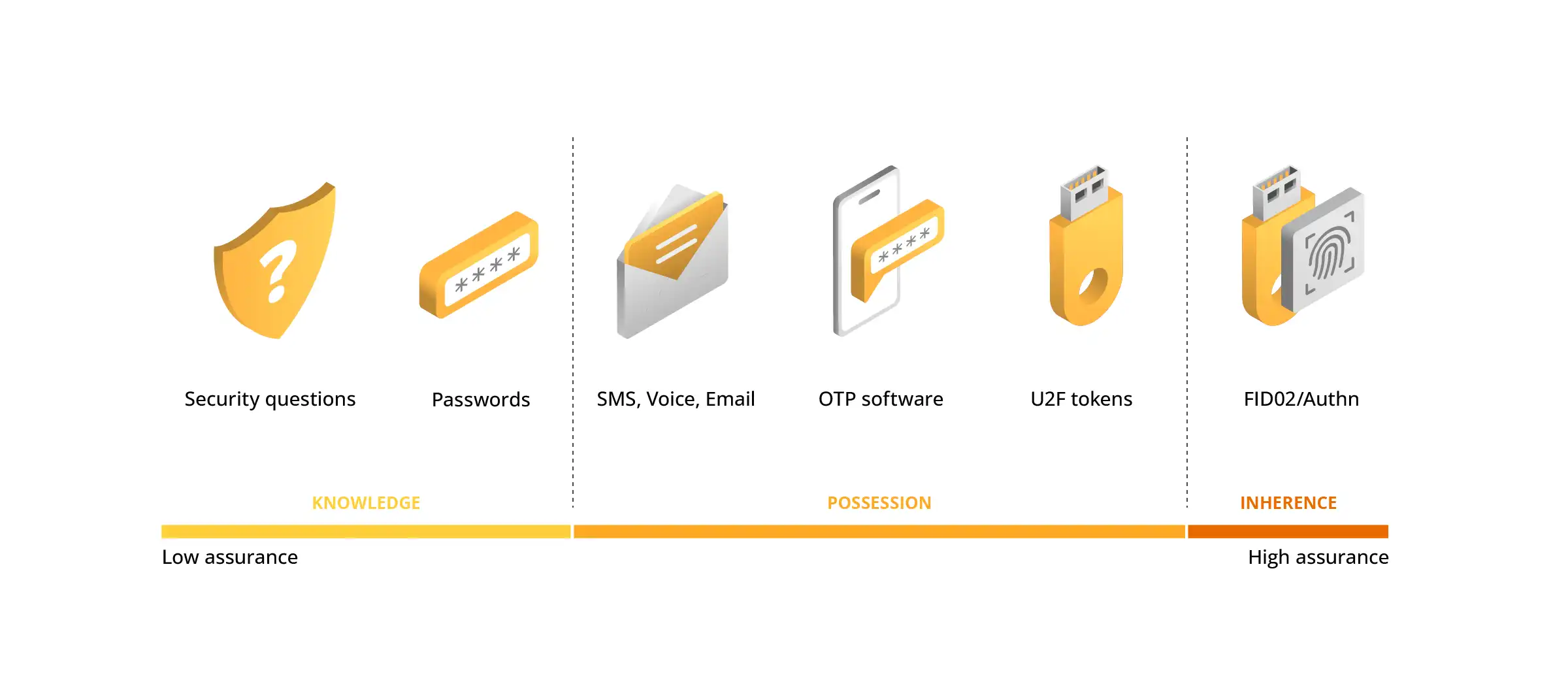
Fig. 2: MFA methods breakdown by security level
Adaptive access control solutions are also increasingly being used, extending the capabilities of MFA to provide better protection under a zero trust approach. It allows security requirements to be dynamically adjusted based on the login context. Access policies can take into account factors such as the user's location, device, risk level, and even the security status of the hardware from which the login occurs. This ensures that MFA is not applied in the same way in every situation, but instead adapts to the actual threat level.
2. Data Classification and Data Leakage Prevention (DLP) Systems
Data classification and data leakage prevention (DLP) systems are key security elements in the modern workplace, especially where sensitive information is processed and employees have flexible access to data from different locations and devices. Data classification is the process of assigning appropriate categories to different types of information (e.g., public, confidential, restricted), in order to determine the level of required protection more accurately. Data leakage prevention (DLP) systems, on the other hand, monitor and control the flow of this data to avoid accidental or intentional leakage of information outside the organization.
Modern data classification systems can operate in an automatic mode, analyzing the contents of documents and applying appropriate labels, such as “confidential” or “for internal use only”. In some cases, users can do this themselves after appropriate training. However, automating security processes reduces the risk of human error and the need for manual monitoring of data operations, easing the burden on IT teams.
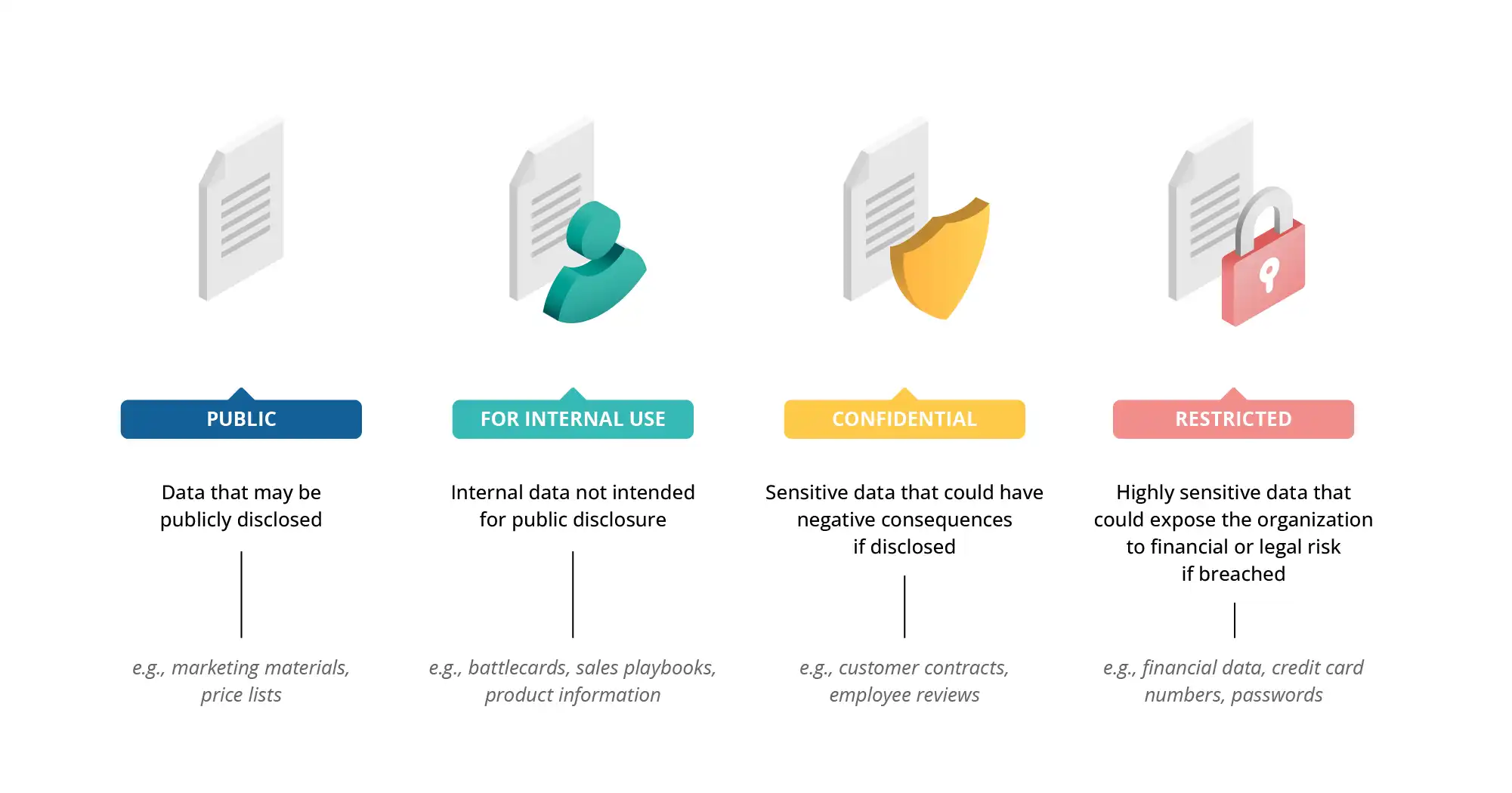
Fig. 3: Example data classification levels
Implementing these mechanisms is particularly important in the context of regulatory requirements such as GDPR, which requires organizations to protect personal data and sensitive information. However, remember to strike a balance between security and the ease of use—overly restrictive policies can block daily operations and reduce productivity.
3. Advanced End Device Protection: EDR and XDR
The sophistication of today's cyber threats means that traditional anti-virus software is no longer sufficient to protect your organization. As a result, solutions such as endpoint detection and response (EDR) and extended detection and response (XDR) are playing an increasingly important role in enabling more effective monitoring and neutralization of threats.
EDR provides real-time detection and response, analyzing files for known threats and monitoring both device and user activity to identify suspicious activity. Unlike traditional anti-virus software, which focuses on identifying threats based on signatures, EDR uses behavioral analysis to detect new, previously unknown attacks.
While EDR focuses on endpoint devices, XDR provides a broader threat context, covering the entire IT infrastructure and integrating data from multiple systems such as the network, email, cloud applications, and user accounts. So instead of analyzing individual incidents, you can see their correlation and detect entire attack campaigns that may span multiple vectors.
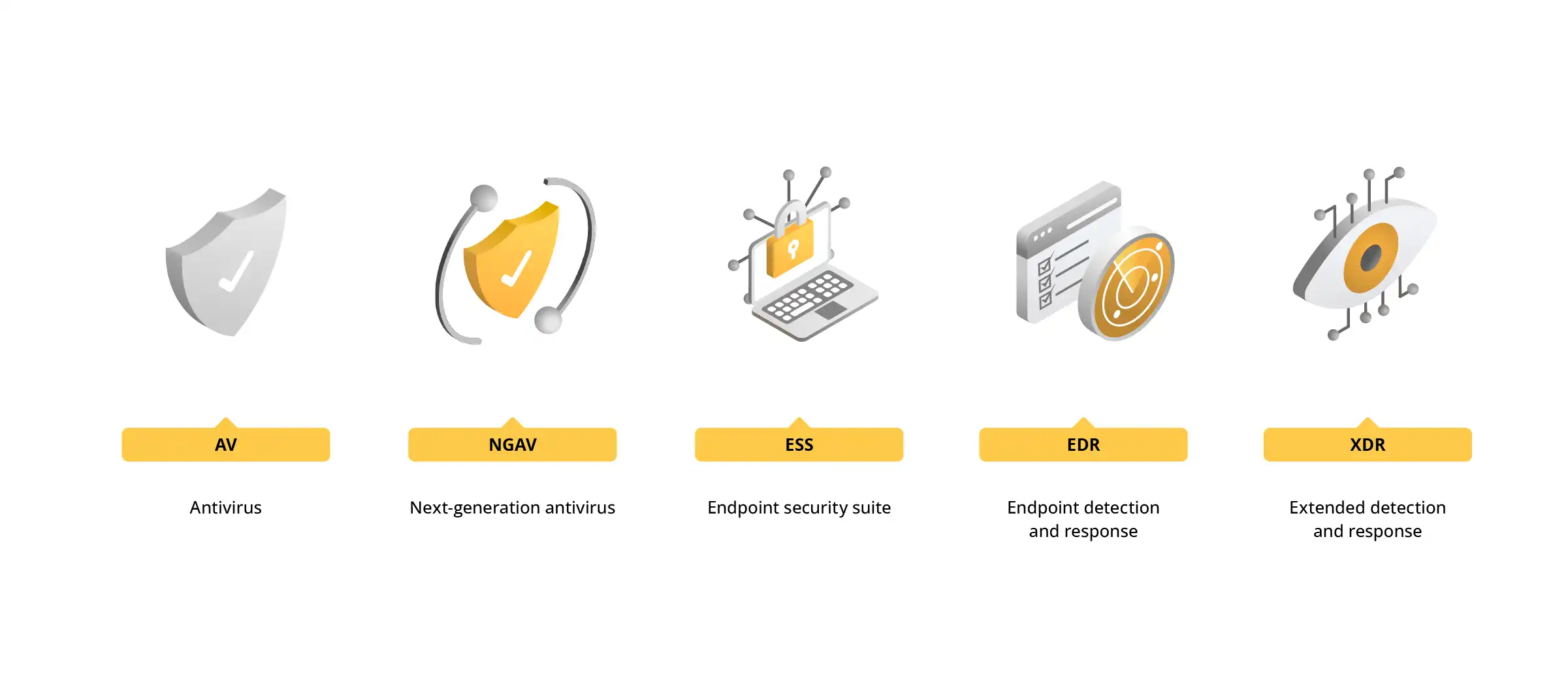
Fig. 4: Evolution of security from Antivirus through EDR to XDR
There are many benefits of implementing EDR and XDR systems, including increased efficiency in threat analysis, reduced number of false positives by automating threat detection and neutralization processes, and—by extension—reduced burden on cyber security teams. However, before making the leap, consider issues such as the need to tailor security policies to the specifics of your organization or to integrate with existing security management tools such as SIEM.
4. Email protection
The vast majority of cyber attacks begin with email, which means that effective email protection is an essential part of a cybersecurity strategy. The use of mechanisms that detect and block suspicious messages before they reach employees is also particularly important in the context of the use of techniques such as business email compromise (BEC), which involves actions taken by attackers after successfully taking over a user account.
Email security systems in use today analyze the content of messages, as well as attachments and links, using spam and anti-phishing filtering mechanisms. The more advanced systems use behavioral analysis and artificial intelligence to detect suspicious communication patterns that may indicate a scam attempt, even if the messages look genuine.
To effectively protect an organization from these threats, it is essential to implement comprehensive email protection systems that scan not only the content of messages, but also links, attachments, and embedded graphics such as QR codes. Some solutions use sender reputation analysis mechanisms, advanced sandbox scanning and technologies that detect impersonation attempts on trusted domains. These systems allow suspicious messages to be blocked at various stages of processing—from delivery to the mail server to user interaction with email content. Effective protection also includes real-time dynamic link checking to neutralize threats even if malicious URLs change their destination pages after the message has been delivered.
5. Management and Security of Endpoint Devices
According to Microsoft's Digital Defense Report 2023, in more than 90% of ransomware attacks, cyber criminals use unmanaged devices to gain initial access to corporate data or perform remote encryption. Endpoint device management is therefore the cornerstone of protecting corporate data and systems. It involves monitoring, controlling, and enforcing security policies on devices used for work, giving the organization complete visibility and control over access to resources.
Today's work environment often includes a bring-your-own-device (BYOD) policy, where employees use personal laptops, smartphones, and tablets for business purposes. While BYOD increases flexibility in the workplace, it is sometimes associated with reduced security, missed system updates, and the use of unfamiliar software. To reduce the risk of attacks, it is best to implement BYOD management mechanisms—enforcing device registration, segmenting data access or separating corporate and personal resources (containerization). This will ensure that corporate information remains protected even if the device does not fully comply with security requirements.
Additional security is provided by virtual desktop infrastructure (VDI), which allows users to access the corporate environment through a virtualized desktop running in an isolated environment, without the need to install corporate applications on the user's personal device.
One of the key aspects of endpoint device management is the ability to enforce compliance with security policies. Organizations can specify security requirements such as mandatory encryption, the use of strong passwords and biometrics, and the execution of anti-virus software updates. In addition, remote management helps mitigate the risks associated with unauthorized software, which can be an attack vector. If a threat or security policy violation is detected, administrators can respond quickly by restricting access to resources until compliance is restored.
6. Cloud Access Security Broker (CASB) and Shadow IT
Today's working environment relies heavily on cloud applications, which offer flexibility, scalability, and the ease of use. However, a lack of control over which applications are used and how they process corporate data can lead to serious security and compliance risks.
To minimize the risks associated with uncontrolled use of the cloud, you can deploy a cloud access security broker (CASB). It will help you:
- identify cloud applications used by employees: detect Shadow IT (unauthorized use of cloud applications by employees) and assess the risks associated with the tool,
- enforce security and compliance policies: restrict access to applications that do not meet the organization's requirements, such as storing data in unverified locations,
- protect data sent to the cloud: implement data encryption, data classification, and data loss prevention (DLP) mechanisms to prevent uncontrolled sharing,
- secure access to cloud applications: enforce multi-factor authentication (MFA) and analyze user behavior to detect suspicious activity, such as unusual logins from outside the corporate network.
Shadow IT is often the result of a lack of official tools that meet users' needs. To reduce the use of unauthorized applications, organizations should not only block access to risky services, but also provide employees with secure alternatives.
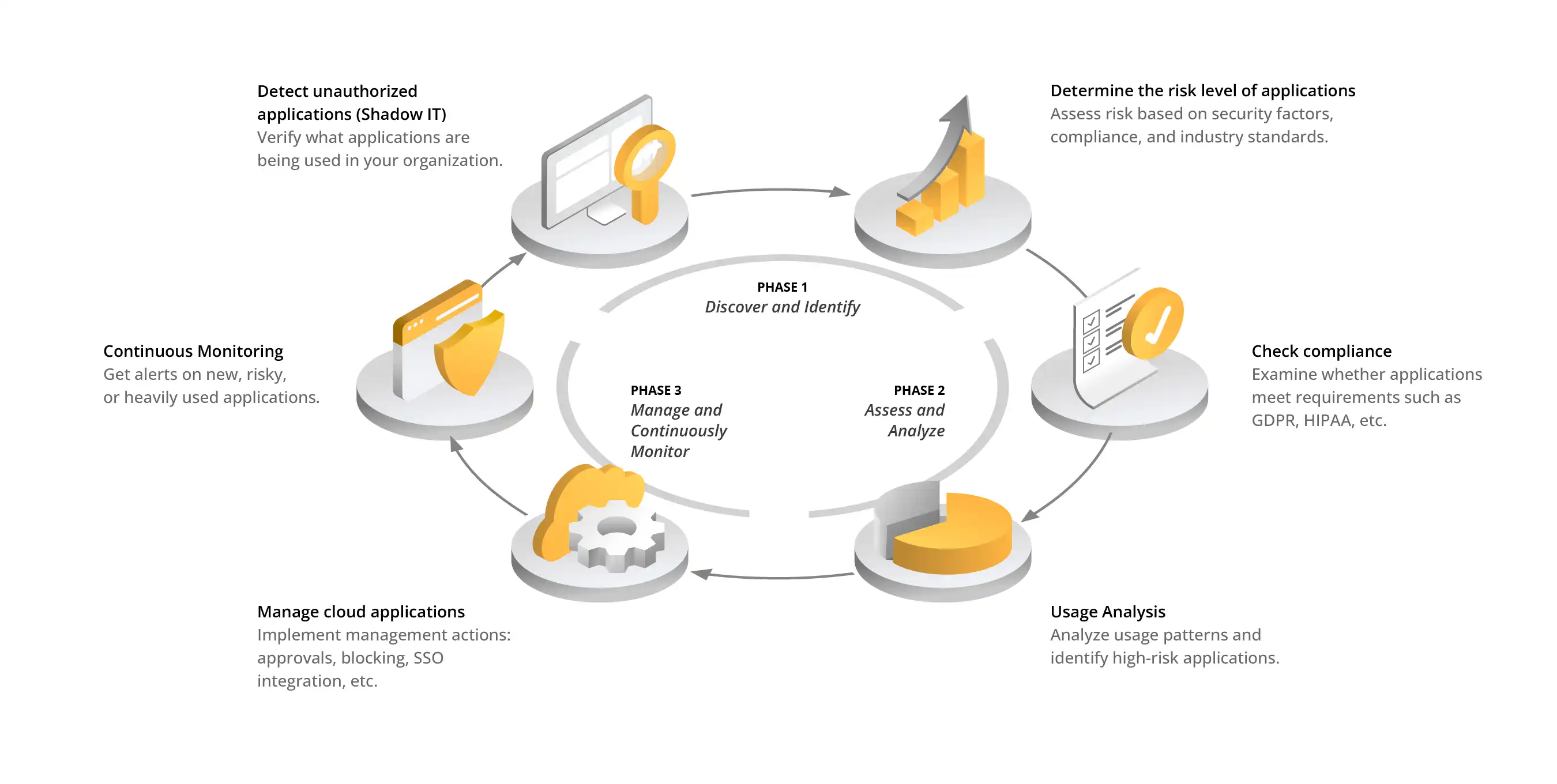
Fig. 5: How to manage Shadow IT?
7. Privileged Access Management (PAM)
Every organization has accounts and privileges that have elevated access to systems, data, and IT resources, such as server administrators, database operators or employees who manage cloud systems. Due to the wide range of privileges, those accounts are a prime target for cyber criminals—their takeover can enable privilege escalation, the installation of malware, the manipulation of data or the complete takeover of an organization's infrastructure.
By implementing privileged access management (PAM) mechanisms, you can minimize the risk by tightly controlling who, when, and how administrative privileges are used. This includes:
- the principle of least privilege: it assumes that the user is given access only to those resources that they absolutely need to perform their tasks,
- the just-in-time (JIT) and just-enough-access (JEA) methods: they allow privileged access to be granted only when it is actually required and to the extent necessary to perform a specific task,
- recording and analyzing the administrator’s activities: enables a rapid detection of suspicious activity and real-time response to potential threats,
- the separation of roles and accounts: administrators should have two separate accounts (one for day-to-day work and one for performing administrative operations), which reduces the risk of an attacker taking over the account,
- access auditing and automating the process of granting privileges: in many organizations, administrators also have broad privileges over SaaS services and cloud infrastructure, which can pose a serious threat if not properly restricted.
More Than Cybersecurity
Implementing the Modern Workplace security mechanisms described above not only strengthens your organization's protection against cyber threats, but also plays a key role in meeting regulatory requirements such as DORA and NIS2. These regulations focus on ensuring the organization's business continuity, effective risk management, and the protection of systems and data from cyber attacks. In practice, this means implementing advanced data protection mechanisms, managing access, and monitoring incidents, reflected in solutions such as multi-factor authentication, privileged access management, email protection, and vulnerability management systems.
DORA and NIS2 compliance also requires continuous threat monitoring and rapid incident response, underscoring the importance of EDR/XDR systems, log analysis and endpoint device management policies. Organizations must not only implement appropriate security, but also ensure that it is regularly updated and adapted to the changing cyber threat landscape. In the face of an increasing number of attacks, these regulations are driving companies to adopt a zero trust approach, which involves strict control of access to resources and continuous verification of user identities.
If you want to learn more about the NIS2 directive, check out our expert article:
Summary
Modern Workplace requires a comprehensive approach to security in terms of advanced protection technologies as well as continuous monitoring and rapid incident response. Implementing mechanisms such as multi-factor authentication (MFA), data classification, DLP systems, privileged access control, and log monitoring creates a robust layer of protection that helps reduce the risk of attacks and helps organizations meet regulatory requirements such as DORA and NIS2.
However, implementing security is only the first step—ongoing threat monitoring and effective incident management are equally important. That's why more and more organizations are opting for services such as SOC as a Service or CTI as a Service, which provide incident analysis, threat prioritization, and immediate response to real attacks. By ensuring that their IT infrastructure is always professionally protected, no matter where or how employees are working, they enable organizations to focus on their core business activities. If you are looking for answers to how to effectively protect your business against cyber attacks, or need help implementing the right security mechanisms, contact us using the form below.